Citrix NetScaler Application Firewall is a comprehensive ICSA certified web application security solution that blocks known and unknown attacks against web and web services applications. NetScaler supports a good range of AppFirewall security checks that can be customized according to the need. But, what do you do, when you want to have aggregated view of these violations with graphical analytics?
Command Center collects these AppFw system logs generated on NetScaler appliance, produce comprehensive graphs and provision built-in reports to provide a top view picture of what violations are being generated.
The steps to get these reports on the Command Center device are very straight forward. In this blog we will encompass all the configurations that need to be done on NetScaler for report generation on Command Center. In a nutshell, you just need to configure Command Center as the Syslog server on NetScaler and you are just a login away to view the violations on the Command Center setup.
NOTE: In this blog, we are assuming that you have configured the AppFirewall setup on the NetScaler appliance.
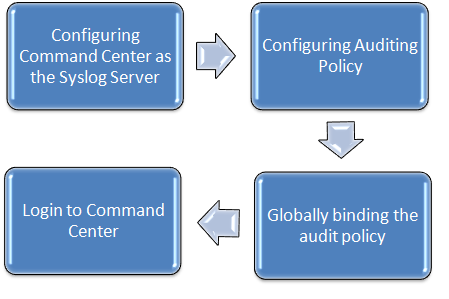
Just to give you a preview, below is the process flow of how to generate AppFw reports on Command Center.
Step 1: Configuring Command Center as the Syslog Server
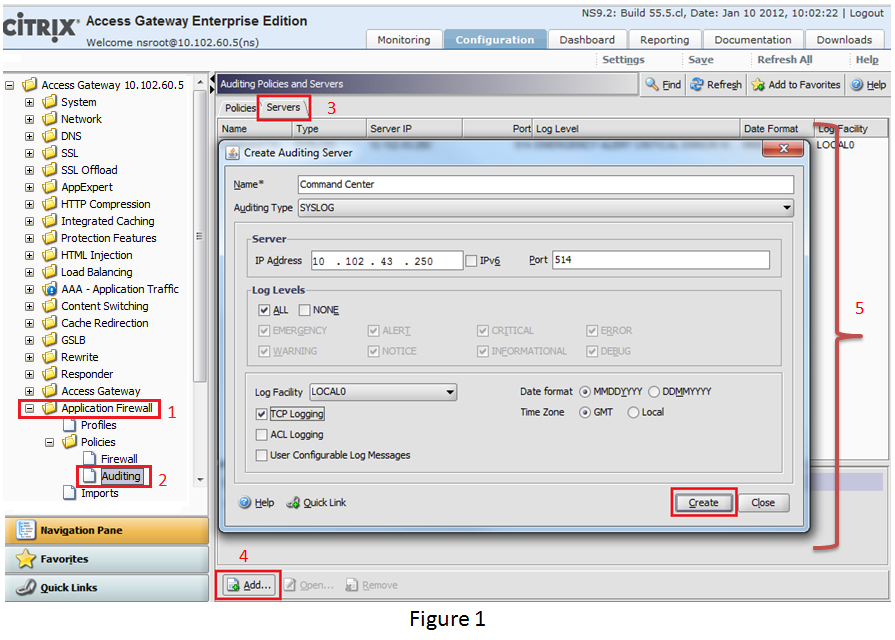
Command Center does AppFw reporting based on Syslog data collected from NetScaler. To have any kind of AppFw reports generated on Command Center, the first and foremost step is to ensure the existence of command center to the NetScaler appliance. To do so, we need to configure Command Center as an auditing Server on NetScaler appliance. This will redirect the syslog’s generated on NetScaler to the Command Center device.
As can be seen, Figure 1 illustrates the steps to configure Command Center as the syslog server on NetScaler appliance via NetScaler GUI. While creating auditing server, ensure that the Auditing Type is selected asSYSLOG.
Step 2: Configuring Auditing Policy
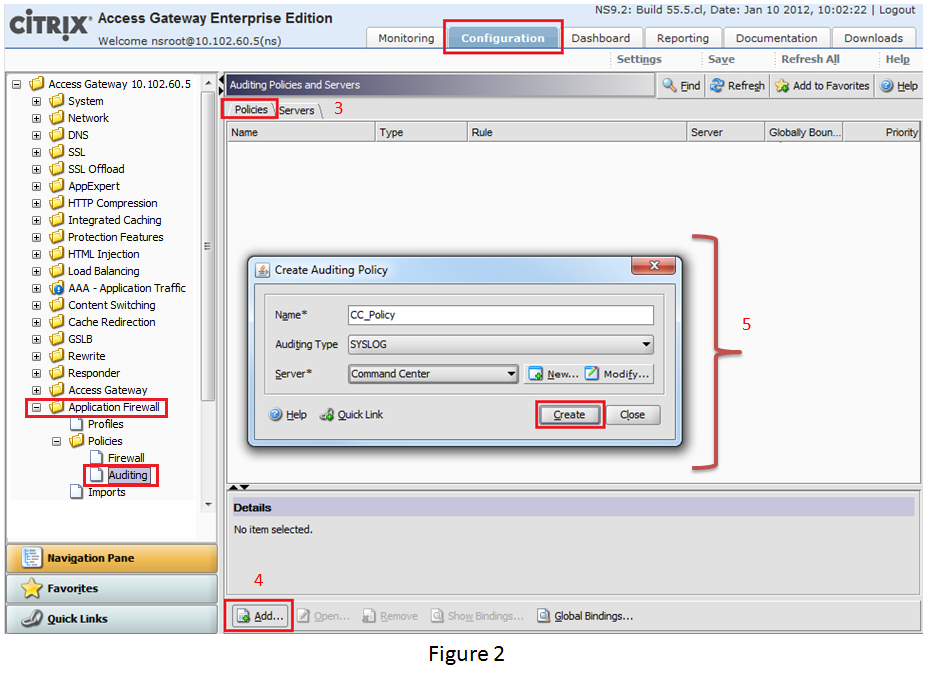
In this step, you need to create an Auditing Policy. Go to Application Firewall>> Policies >> Auditing in the Navigation Pane on the left. Select Policies tab beside the Server tab. ClickAdd, mentioned at the bottom of the window. SelectAuditing Type as SYSLOGand Server as Command Center syslog server configured in the Step 1and click Create. This Audit Policy defines the protocol type and Server definition defines what logs are sent where.
Step 3: Globally Binding the Audit Policy
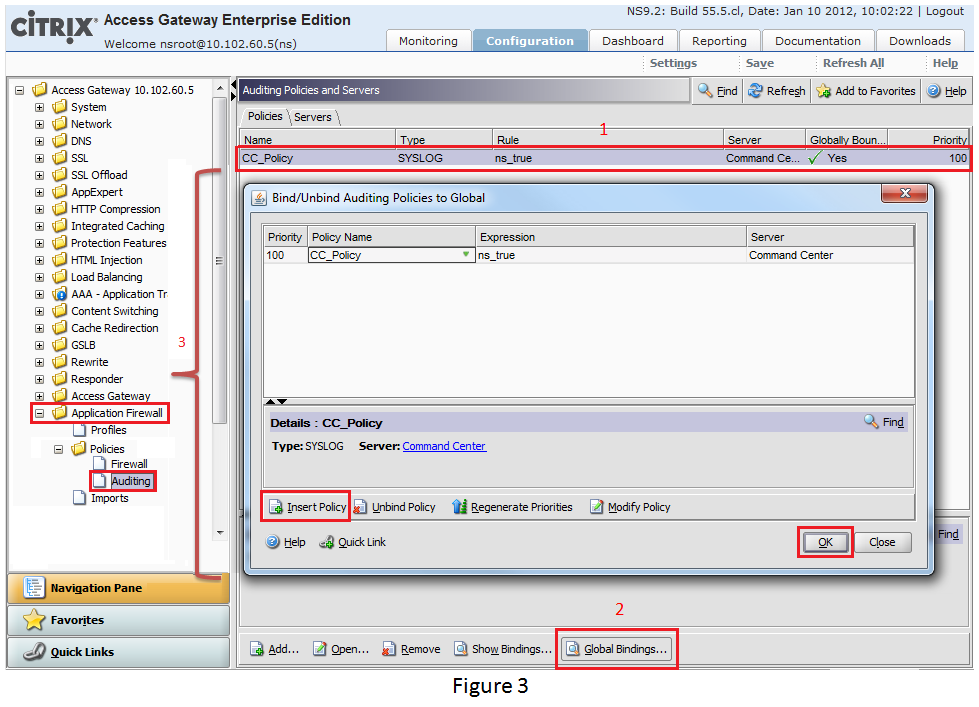
After defining the Audit Policy, you will need to bind the audit policy globally to ensure logging for all NetScaler AppFw system events. To do this, select the defined policy, click Global Bindings (mentioned at the bottom of the window) and click Insert Policy to select the defined audit policy defined in Step 2. Click OK.
NOTE: Save the configuration done till now on NetScaler appliance by clicking Save (mentioned at the top right of the window).
Step 4: Login to Command Center
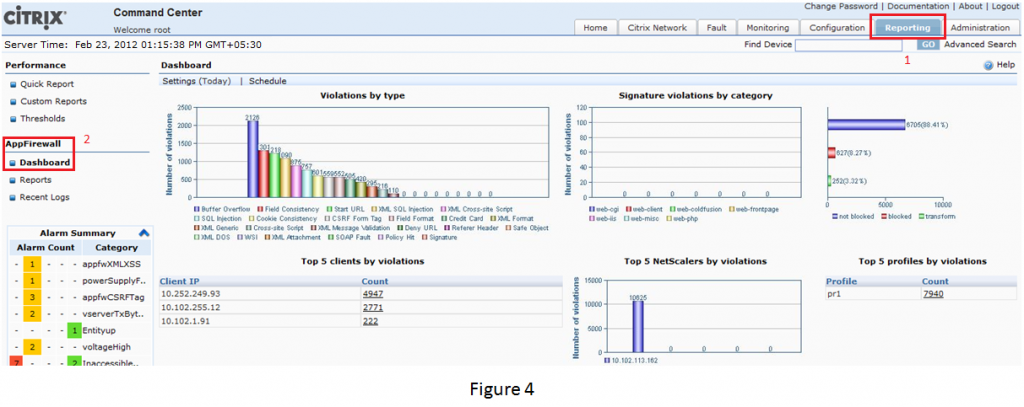
Now, last and the most important step is to login to the Command Center device, go to Reporting,thentoAppFirewall’s Dashboard and see the violations generated on NetScaler, are also reflected on Command Center’s AppFirewall Dashboard :).
With these simple steps you will be able to generate and sync the violations generated on NetScaler and the violations reflected on these graphs.
Note that, the dashboard will start populating data from the time you configure everything from step 1 to step 3 onwards only. It won’t report the violations on Command Center before these setup configurations are done.